Humanising the IoT World
When Kevin Ashton from Birmingham, England, coined the term “Internet of Things” in 1999 in a presentation to Proctor & Gamble executives while working on an RFID project to better manage the supply chain at P&G he surely could not have imagined the enormous impact this was going to make for humankind, let alone think about humanising the IoT world.
Interestingly, Kevin preferred the term “Internet for Things”, which I find much more appropriate as, if we consider the Internet as an enabler for the things to be connected, then the network is important, but the participants are critical.
According to an article at iotforall.com, the total number of connected IoT devices worldwide is expected to reach 14.4 billion by the end of 2022. Let’s think about that for a second. This is staggering when one considers that the population on this planet is around 8 billion. And if we look back, there has been a notable shift from connected non-IoT devices to connected IoT devices over the last decade.
The number of connected IoT devices had surpassed connected non-IoT devices as we experienced the Covid-19-induced lockdown in 2020 from just 9% of total devices in the IoT devices ‘bucket’ in 2010 to 54.2% – a fivefold increase – in 2020 as researched by IoT-analytics.com.
Zooming into some of the fundamentals and intrinsic details of the IoT world, the way I see it is that there are four fundamental pillars to IoT:
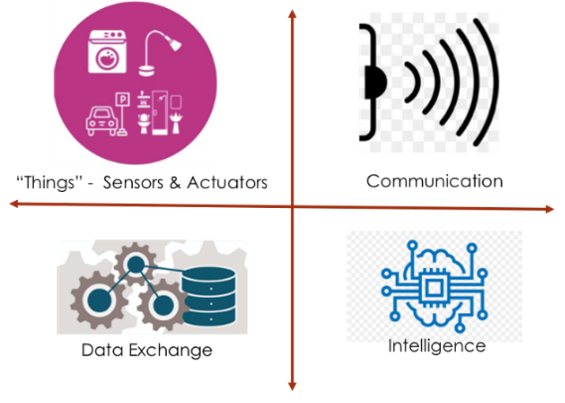
What I would like to focus on for now is the Data Exchange pillar, as that is what is at the heart of, and the purpose of, IoT devices: the exchange of data. According to Statista, by 2025, connected IoT devices are expected to generate an astonishing 79.4 ZBs (zettabytes) of data. As you may know, the number of bytes in a ZB is 1 followed by 21 zeroes, or 1,000,000,000,000,000,000,000. To put that into perspective, if each byte is represented by a millimetre, then 79.4 ZB is 176 million round trips between Earth and Mars.
Beyond all these numbers, as huge and fascinating as they are, there are real humans, with their real lives, and their real stories, and that’s what is most interesting to me; I truly believe that every technology that we have should be humanised. The IoT revolution is redefining what we call our homes and how we spend our time doing everyday activities in our homes. Here is a home with connected devices:
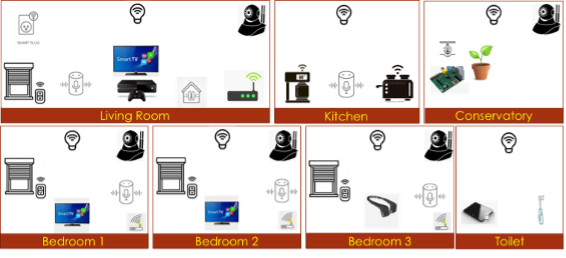
It features connected light bulbs in all the rooms for precise control of light with the convenience of voice activation, connected thermostats that can make heating more efficient and – hopefully – less expensive by being able to control it from anywhere in the world, connected toasters and coffee machines in the kitchen, a connected weighing scale which can help us control our weight and a connected toothbrush in the bathroom (perfect for gamifying young children’s brushing) and connected smart blinds to connected plant watering systems – you name it, it seems you can have it connected.
Without a doubt, the proliferation of these connected devices in our daily lives is making our daily routines easier, more convenient, and more fun, of course, in a positive way. At the same time, these connected devices and the enormous amount of data generated by them create great challenges…
Safe, not sorry.
In October 2018, Medtronic, an American medical device company, had to disable the remote update of two of its pacemaker devices amid concerns that they may be vulnerable to hackers – we’re sadly all too often used to financial hackers stealing money, but I cannot even imagine the implications if an implanted pacemaker inside a human were compromised.
As reported by Kaspersky, between January and June 2021, 1.51 billion breaches occurred with IoT devices, most of which happened through Telnet remote access. I have personally been impacted by this in 2018 when the connected IP camera in my house was breached through Telnet. I spoke about how this happened in my TEDx talk in September this year.
With connected devices enriching our houses with “smart” tags, many of the order initiation transactions will be initiated by these devices. For example, the smart washing machine may send an order to an online store for washing powder when it senses low inventory, or the moment you realise you are low on milk is when it arrives, ordered by your fridge, at the door.
It is fascinating to imagine the convenience it will bring about, not to mention, for the online stores – and I’m thinking of one huge, very well-connected one in particular – a lucrative revenue stream. Still, we will need to be careful in this world of connected machines, as the data they are exchanging has important security implications if not protected…
Let’s take a simple example of electricity and water smart meters sending data to the service providers for the obvious convenience afforded to the consumer – no more meter-reading, for one thing – but is the data being sent not sensitive though? That data, if not protected, can perhaps be used to profile the properties to identify when they are occupied and when they are not, to allow targeted telemarketing calls, or even worse – if that data is leaked to the dark net, it can be used by burglars for targeting unoccupied properties at the time.
How do we humanise the IOT world?
So, if we are humanising the IoT world, what is that important something which we must not overlook? It is the human perspective. We need to humanise the IoT world, including a bridge between these connected IoT devices and the humans that use them, or who rely on them.
The omnipresent mobile phone may be the most suitable way to enable that human/machine bridge. How? These devices are associated with a humanised identifier: the mobile phone number.
Then, we can re-use services like Sekura’s SAFr Auth to authenticate the genuine owner of the connected device and the data, enabling trust in a simple, secure and above all, humanised way. We can extend the process to add authorisation as the next step, so the human owner of the data can authorise the transmission of the data generated by these devices, using the same ubiquitous mobile phone, thereby humanising the IoT world.
For context – authentication is a challenge to the user to prove they are who they claim to be, and authorisation is a request to the authenticated user to perform some actions, like transmission of data. Thanks to the mobile phone, the humanisation of IoT is already here.
Quoting Albert Einstein, “We cannot solve our problems with the same thinking we used when we created them”.
Let’s think differently.
With coverage across 5 continents, Sekura Mobile Intelligence is the leading global provider of mobile identity solutions, providing trusted, secure, and easy-to-consume solutions for ID verification, anti-fraud and secure online authentication use cases. Sekura works with established KYC, identity verification and risk data providers who have already integrated into leading global brands with demand for mobile identity solutions.
Through the integration of real-time mobile data into our partners’ existing services, we enable them to extend and enhance their customer offerings into new services, use cases and geographies through the adoption of SAFr, our single standards-based, mobile intelligence API.
To offer your customers the opportunity to benefit from our global mobile identity solutions, contact the Sekura team today.


